Flywheel is managed WordPress hosting built for designers and creative agencies to build, scale, and manage hundreds of WordPress sites with ease. One can set up a WordPress site in less than two minutes without any complex configuration. But Flywheel PaaS is vulnerable to subdomain takeover issues, I am publishing this write-up because I didn’t find any fingerprints/writeups regarding this anywhere on the internet. So thought to do it for the infosec community.
I discovered this issue last year during the security assessment/ VAPT project; since I didn’t found any resources or information about the Flywheel subdomain takeover issue, I chose to give it a try on my own.
By reading the Flywheel Documentation and mechanism to verify domains, I was almost sure that this is a potential subdomain takeover but I planned to create a proper proof of concept.
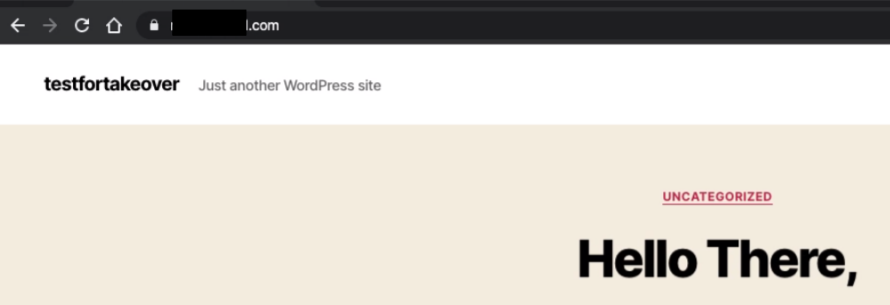
The vulnerable subdomain homepage looked like this:
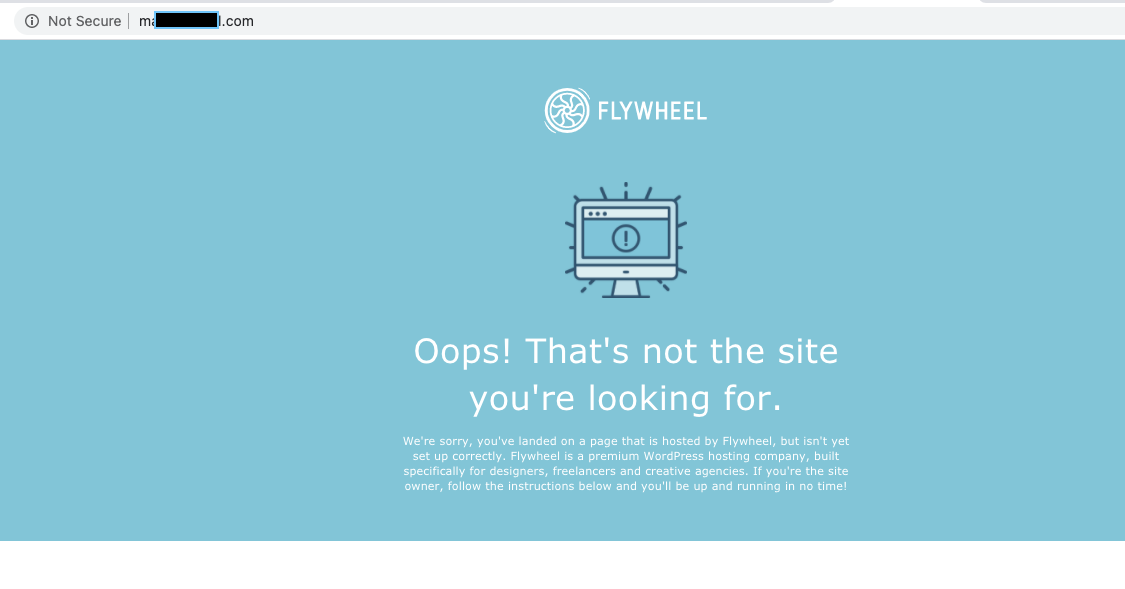
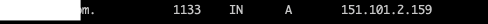
The vulnerable subdomain had an A record pointed to Flywheel PaaS.
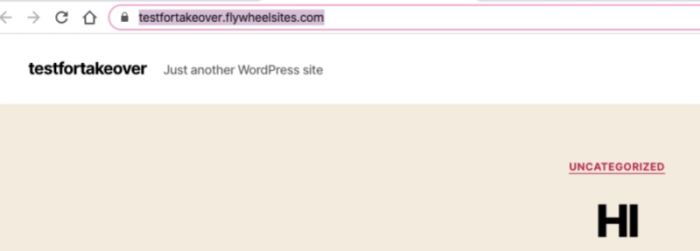
I created an account at https://getflywheel.com/ and purchased a plan to test the subdomain takeover issue. (It was a gamble of $15)
Created a simple wordpress site with minimal effort.
Tried connecting subsdomain with wordpress instance.
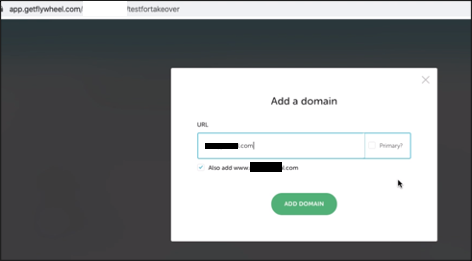
And here we go.
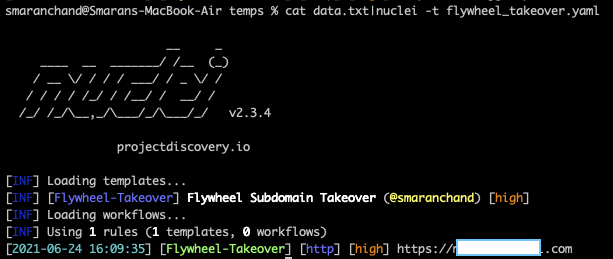
Since there aren’t any resources or writeups regarding the Flywheel subdomain takeover issue, I planned to do a writeup as well as create a nuclei template for the detection of this vulnerability. Hope to see this template in the nuclei repository soon. For now, below is the template to use.
id: Flywheel-Takeover
info:
name: Flywheel Subdomain Takeover
author: smaranchand
severity: high
tags: takeover
reference: https://smaranchand.com.np/2021/06/flywheel-subdomain-takeover
requests:
- method: GET
path:
- "{{BaseURL}}"
matchers:
- type: word
words:
- "We're sorry, you've landed on a page that is hosted by Flywheel"
- "<h1>Oops! That's not the site<br>you're looking for.</h1>"
condition: andSave the content as anything.yaml and use it with nuclei.
Severity: High
Impacts: An attacker can use this misconfiguration to takeover the subdomain, publish arbitrary contents, run malicious javascript code at the user’s end, harvest credentials using phishing attack, deface a website, etc also steal the cookies of the user if cookies are scoped to the parent domain and escalate to account takeover.
Remediation: The DNS entry for the subdomain should be removed from DNS records if not in use.
Do share if you liked, Let me know if you have any questions regarding this.
Thank you so much for this blog man,I just got my first ST from it,wouldn’t have managed without your help.You’re a champion.
Hello, how is everything? I have a bug bounty situation where nuclei warned me of the failure I registered the $15.0 login on the flywheel but I can’t make the note.
Hello Fernando,
Thanks for asking, how are you doing? I might be able to help you, Would you please share the DNS records over the DM on Twitter?
Regards,
Smaran
Of course, I sent a tweet but I couldn’t send a private message.