During the Vulnerability Assessment Penetration Testing(VAPT) assessment of an organization’s assets, I encountered an interesting issue that led to flaws observed in all the projects accomplished by the Vendor/Development agency. While security assessment engagement, I discovered an unprotected Opensource file manager exposed publicly on the corporate website of an organization. A malicious user can upload, edit, and delete the files saved within the webserver. Tracking down the vendor for the Content Management System (CMS), I was surprised to know that the vendor has provided the services to more than 17+ organizations with a similar codebase and dependencies in the web application without even a single change in path, endpoint & parameters.
The vulnerability was due to unprotected Filemanager, elFinder, where users can browse, edit, and modify the contents. For the worst part, this vulnerability can be escalated to achieve Remote Code Execution(RCE) in the webserver. More details about the vulnerability are provided by at SonarSource blog.
Based on the web response and the endpoint used by the file manager, I created a nuclei template to detect and verify this vulnerability automatically.
id: elFinder-filemanager-exposed
info:
name: elFinder Exposed
author: smaranchand
severity: high
tags: exposed-panels
reference: https://smaranchand.com.np/2022/01/organization-vendor-application-security/
requests:
- method: GET
path:
- "{{BaseURL}}/assets/elFinder-2.1.9/elfinder.html"
- "{{BaseURL}}/assets/elFinder/elfinder.html"
- "{{BaseURL}}/elfinder/elfinder-cke.html"
- "{{BaseURL}}/admin/elfinder/elfinder-cke.html"
- "{{BaseURL}}/uploads/elfinder/elfinder-cke.html"
- "{{BaseURL}}/uploads/assets/backend/elfinder/elfinder-cke.html"
- "{{BaseURL}}/uploads/assets/backend/elfinder/elfinder.html"
- "{{BaseURL}}/assets/backend/elfinder/elfinder-cke.html"
- "{{BaseURL}}/backend/elfinder/elfinder-cke.html"
- "{{BaseURL}}/uploads/assets/backend/elfinder/elfinder-cke.html"
matchers-condition: and
matchers:
- type: word
words:
- "elFinder"
- "php"
condition: and
- type: status
status:
- 200Although I planned to push this template to the Project discovery’s official nuclei repository, some false positives popped up to deal. So as of now, you can download the template from my Github repository.
Using the simple google dork, I gathered the list of the vendor’s clients and ran the template on all target lists provided below results.
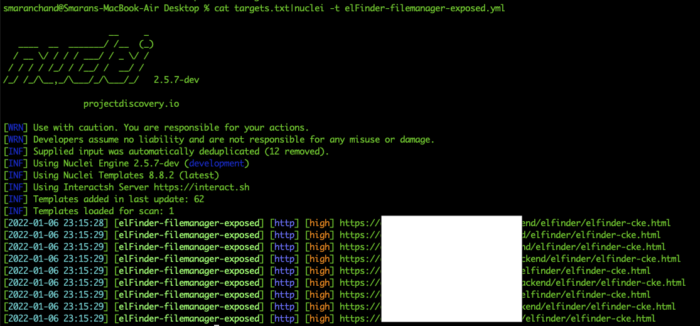
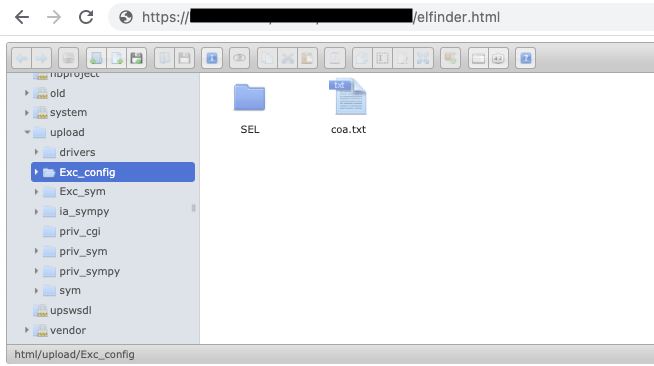
Accessing the vulnerable endpoint resulted in unrestricted access to the file manager.
The below screenshot demonstrates the escalation to RCE via uploading a malicious PHP file, kudos to my team member Pr3d@t0rx for this.

In other words, it was possible to achieve Remote Code Execution(RCE) on all of the vulnerable websites developed by the same vendor, which could have had a tremendous impact on the industry if exploited by a malicious user. After contacting the vendor with a well-documented report and important stuff, By understanding the criticality & urgency of the situation, the vendor patched the issue in all the scopes where vulnerable components have been used.
Remediation
For Organization
The organization should ensure the web application’s security before deployment if the product is built with a secure architecture design, passes the security assessment, and meets compliance. Furthermore, the organization should periodically conduct an internal Vulnerability Assessment and penetration Test(VAPT) and patch the vulnerabilities.
The enactment of defensive technologies like Web Application Firewall(WAF), IDS, IPS, SIEM must be done. Additionally, regular monitoring of the assets should be prioritized. The formation of a Security team in the organization is as important as other departments. The team of offensive security engineers, security analysts, and software security engineers ensures the secure state of the organization and consistently adds value to the organization.
For Vendor/Development firm
The vendor/development firm should mold the product with secure architecture, including components, dependencies, and Secure Coding Practices, so that product would not be vulnerable to the OWASP top ten vulnerabilities. Making Security Testing a crucial part of the software development life cycle would be the best to secure from breaches and security incidents.
“Writing a secure web application starts at the architecture phase. A vulnerability discovered in this phase can cost as much as 60 times less than a vulnerability found in production code.”
Andrew Hoffman, Web Application Security: Exploitation and Countermeasures for Modern Web Applications
Some of the important processes that development firms should focus on are Operating the Security Assessment using Static Application Security Testing (SAST) & Dynamic Application Security Testing (DAST) tools on the product throughout the Software Development Life Cycle(SDLC), which will genuinely improve the quality and security posture of the product.
Creating the specific job or expertise for the role of Software Security Engineer/ Application Security Analyst in the organization is worthwhile.
The compliance, policies, and procedures can initially lower the risk of security threats through proper implementation. The decisions made disregard of security perspective open a way for lousy people to harm the system, which are the recurring threats that can lead to the biggest hack of all time anytime soon.
Please let me know your thoughts about the enrichment of web application security and comments about the write-up.