On September 3rd, 2022, We organized the very first meetup of OWASP Kathmandu local chapter. Our(I and Corrupted_brain) minds were bursting with hundreds of ideas to make the event interesting and fruitful. Finally, We choose to embed a secret CTF link in the Badge for attendees and speakers which came out to be like this.

If you will zoom in and see, there is a bitly URL on the rightmost bottom side of the badge. Which is https://bit.ly/owaspktm but sadly none of the attendees noticed and visited the URL. Well, it wasn’t something we were expecting from the security enthusiast, especially from the hacker mindset people.
Since we didn’t receive any solves or hits in the URL from the past 3 hours of the event we decided to provide information about a hidden CTF. Trust me, the environment was crazy when we announced it. Attendees were trying everything to find the CTF from scanning the Networks like Wireless/Bluetooth to sneaking through the walls of the conference hall and WIFI scan QR code, but few of them only knew that the challenge link was hanging right in their necks in a badge with a lanyard.
The challenge was designed simply, which requires a single but logical step to acquire the CTF flag. Also, we created it ephemeral by design, first, come first priority. The attendees will have to visit the URL in the badge which will route to https://hacknopedia.com/ctf/
The page is designed to disguise users, it looks like a 404 server error but it’s not what we always see, the source of the page has some juicy information.
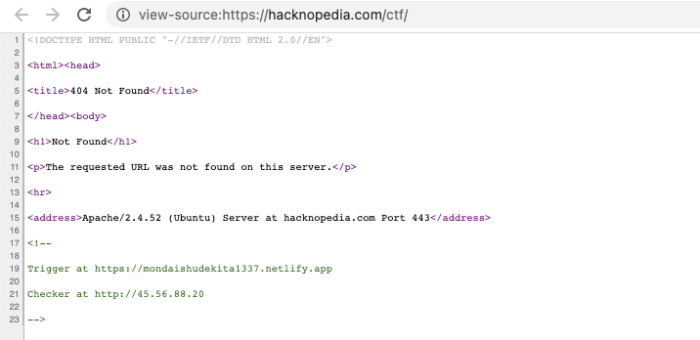
What could be the logic? Trigger and Checker?
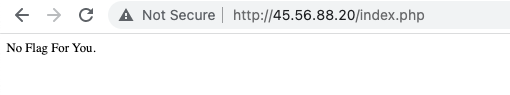
The Checker URL http://45.56.88.20 will show the message “No Flag For you” and the Trigger URL http://mondaishudekita1337.netlify.app is where something needs to be done. We uploaded the source code to index.html page so that players will understand the logic.
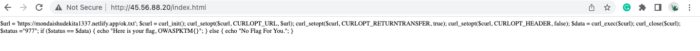
Beautifying the code for a better view:-
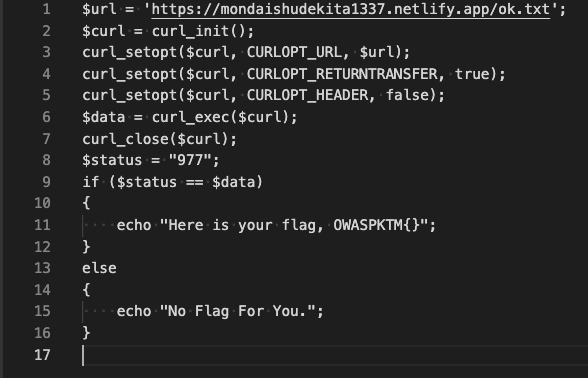
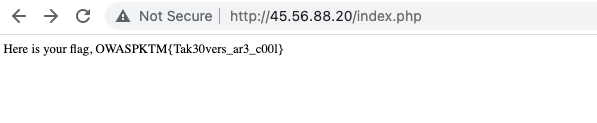
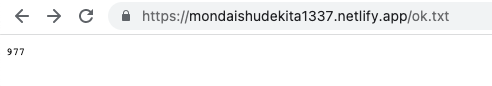
From the above snippet of code, One can clearly see that the checker which is http://45.56.88.20/index.php will send a curl request to host http://mondaishudekita1337.netlify.app/ok.txt internally and if the output is matched with the value of variable “status” which is 977, The Checker will dispense us a flag.
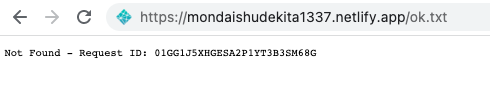
Basically, the output of the http://mondaishudekita1337.netlify.app should be controlled, and a text file ok.txt with content “977” must be placed inside so that it will fulfill the checker’s condition and dispense the flag.
I was surprised to know it was actually a point where most of the CTF players were unable to think about controlling the host. The idea was simple to create a Netlify app with the name mondaishudekita1337 and upload a file named ok.txt with content “977” in plain text and execute checker. In other words Netlify app takeover !!!
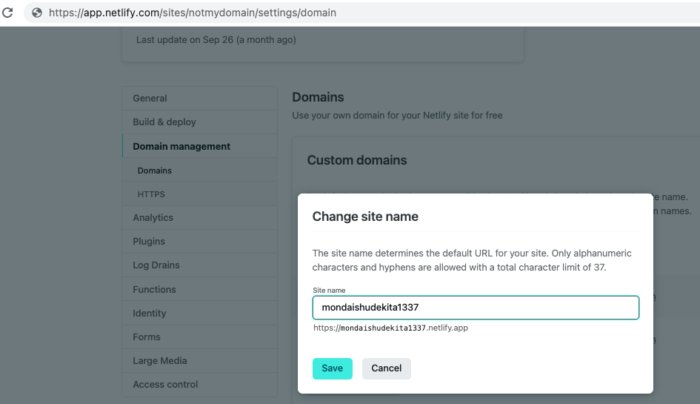
And upload a filename with ok.txt in the root directory.
Finally, after providing a few hints a team managed to take over the host and get the flag.