I have seen most of the peoples searching for No rate limiting issue at endpoints like password reset resulting into mass email triggering, SMS triggering or sometimes abusing it for other common activities.
When it comes regarding No rate limiting issue in API or web endpoints I must say “All you need to do is make an impact“. And also i couldn’t forget the issue one of my talented friend (Name Removed) 😀 found in one of the ISP site resulting to free internet usage for a lifetime. That was a nice issue regarding No Rate Limiting/Security Misconfiguration.
Although I am not happy writing this blog post because the same endpoint had Insecure Direct Object Reference(IDOR) issue which got duplicate. I wanted to let you know all peoples that how I used my common sense and got the bounty.
I found an IDOR at one of the public programs in bugrowd with which I was able to see the personal information as well as cancel some of their pending operations.
POST /api/action/cancelAction HTTP/1.1
Host: sub.xyzcompany.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:67.0) Gecko/20100101 Firefox/67.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 98
Connection: close
Referer: https://sub.xyzcompany.com/page/login/app
Cookie: __cfduid=peepdipeepdibaambaam; REMEMBER_ME_COOKIE=somebiscuitshere
ActionId=25296&&csrf=somethinghere&apiClient=WEBDescending the value of ActionId to valid numeric id canceled the pending actions from respective account having the ActionID. So the bug confirmed and i reported it, unfortunately, it got duplicate after they triaged it
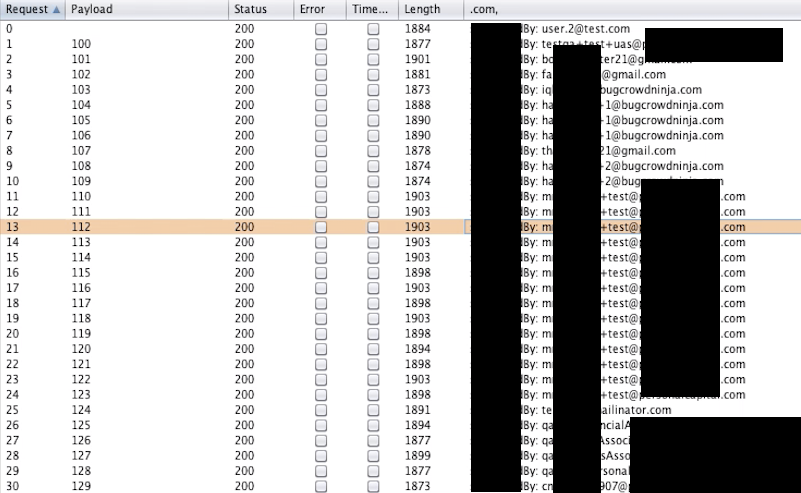
And then I thought to explore some more information so I sent the API request to intruder tab and discovered that I was able to brute the requests at the same time.
I filtered the response of the request by using some regex for printing useful information only. The No Rate Limiting actually led to the disclosure of the user’s information in mass. It also resulted in a mass number of emails to the individual’s mailbox having the same ActionID as reference.
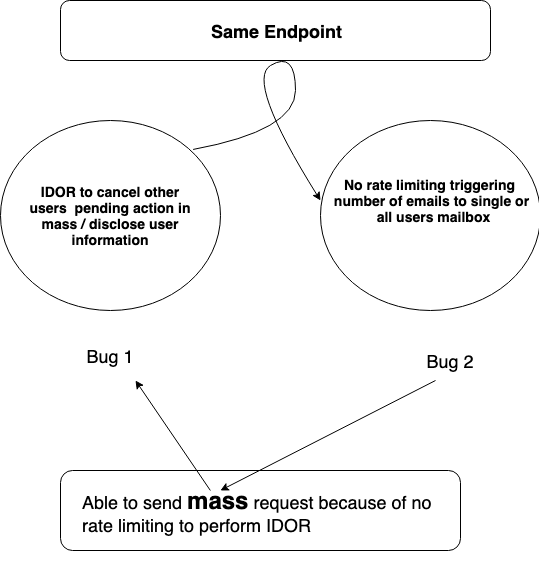
All i meant to say that the main root for disclosing information of mass users was no ratelimit issue due the absence of Rate Limiting I was able to perform two actions at the same time which were canceling others pending operations and spam mass number of emails to any individuals inbox.

They rewarded me an amount with which I can pay my bills for a month.
Do share if this post helped you.
What was that regex code?
You can auto select the required data from the response and generate the regex code from burpsuite’s intruder tab.