When it comes regarding API pentesting, I am always eager to test it even though I don’t succeed to find critical issues.
It was one of the private programs from bugcrowd. It’s the same program where my P1 bug got duplicate. 🙁 And I decided to give it a final try.
Without wasting time I checked the scope and discovered that Android, IOS app and serving API were in the scope.
Once again I fired up my best SSL unpinning tool Frida 😀 and started intercepting the network traffic of Android app. Although I wasn’t able to test the scope fully because of some regional issues and resources required.
While making changes to the account information I found that API was using PUT method to update profile details.
Below is the API request for updating Name
PUT /api/v2/user/xxxxxxxxxxxxxxxxxx/profile HTTP/1.1
Accept: application/vnd.api+json
Authorization: Bearer XXXXXXXXXXXXXXXXXXXXXXXXXX
api-key: xxxxxxxxxxxxxxxx
Content-Type: application/json; charset=UTF-8
Content-Length: 244
Host: api.redacted.com
Connection: close
Accept-Encoding: gzip, deflate
User-Agent: okhttp/3.10.0
{"EmailAddress":"[email protected]","FirstName":"Smaran","Parameter1":"12345","MobileVerified":true,"Mobile":"1234567890","Parameter2":"67890","Surname":"SO","UserId":"xxxxxxx"}The response part disclosed a new parameter “XPoint”:”” without any value.
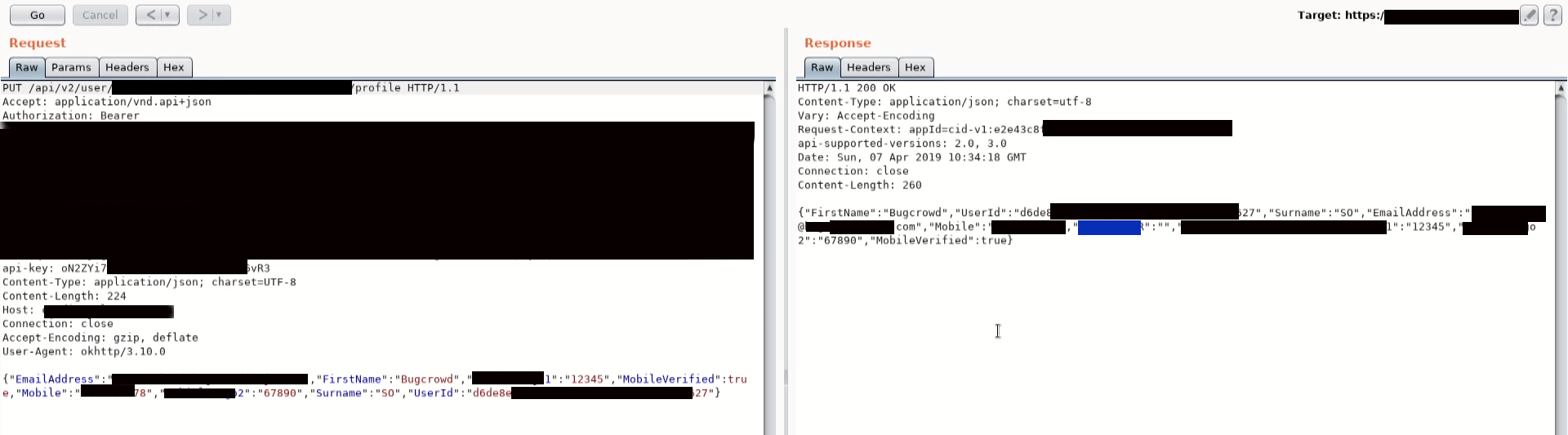
{"EmailAddress":"[email protected]","FirstName":"Smaran","Parameter1":"12345","MobileVerified":true,"Mobile":"1234567890","XPoint":"","Parameter2":"67890","Surname":"SO","UserId":"xxxxxxx"}
As it is clearly seen that a new parameter Xpoint was reflected in the response.
In order to check for parameter pollution issue, I added Xpoint parameter and sent the API request with value 1500 and it reflected “XPoint”:”1500″ in the response 😀
In order to verify the issue, I logged out of the mobile app and logged in again. I found that the Xpoints were still reflecting in my account.
Note: XPoints are the loyalty points collected. So in that scenario i was able to generate any amount of Loyalty points in my account.
This issue might seem easy to find and exploit but you will never know until you don’t do it yourself.